What is Social Engineering?
Social engineering is a **psychological manipulation** technique used by cybercriminals to trick individuals into revealing sensitive information, such as passwords, bank details, or security credentials.
Unlike traditional cyberattacks that rely on technical exploits, social engineering **targets human psychology**, exploiting trust, fear, or urgency to deceive victims.
🚨 Example: A hacker pretending to be an IT technician calls an employee, asking for their login credentials to "fix an issue." Believing it's legitimate, the employee hands over their details—granting full system access to the attacker.
Common Types of Social Engineering Attacks
Phishing Attacks
Phishing is a cyber attack where attackers impersonate **trusted organizations** (banks, IT teams, government agencies) to steal **login credentials, financial details, or personal data**.
📌 How Phishing Works
- 📝 The attacker **sends an email** disguised as a legitimate entity (e.g., PayPal, Microsoft).
- 🔗 The email contains **a fake link** leading to a fraudulent login page.
- 📩 The victim **enters their credentials**, unknowingly sending them to the attacker.
- 🚨 The attacker **gains access** to the victim's accounts and may use or sell the information.
⚠️ Real-World Example: Microsoft 365 Credential Theft (2020)
Cybercriminals used fake Microsoft 365 emails to trick employees into **resetting their passwords** on a **phishing website**. Thousands of accounts were compromised, leading to **corporate data breaches**.
🛡️ How to Identify & Prevent Phishing
- ✔ **Check the sender email** – Look for misspelled domains (e.g., support@mícrosoft.com instead of **microsoft.com**).
- ✔ **Hover over links before clicking** – Verify if they match the legitimate website.
- ✔ **Avoid urgent requests** – Phishing emails often pressure users into immediate action.
- ✔ **Use Multi-Factor Authentication (MFA)** – Prevents account takeovers even if credentials are stolen.
Vishing (Voice Phishing)
Vishing (voice phishing) is a **fraudulent phone call** scam where attackers impersonate IT support, banks, or government agencies to extract **login credentials, financial details, or security codes**.
📌 How Vishing Works
- 📞 The attacker **calls the victim**, pretending to be an IT technician, police officer, or bank representative.
- ⚠️ They create a sense of urgency ("Your account has been compromised! Act now!").
- 🔑 The victim is tricked into providing **login credentials, PIN codes, or personal data**.
- 💳 The attacker **accesses bank accounts or systems** to steal money or sensitive data.
⚠️ Real-World Example: IRS Tax Scam (2019)
Fraudsters impersonating IRS agents **called U.S. taxpayers**, claiming they owed unpaid taxes and threatened arrest if immediate payment wasn't made. Many victims paid using **gift cards or wire transfers**, losing **millions of dollars**.
🛡️ How to Identify & Prevent Vishing
- ✔ **Verify caller identities** – Hang up and call back using the official company number.
- ✔ **Never share personal details over the phone** – Legitimate companies won’t ask for full credentials.
- ✔ **Ignore calls that demand urgency** – Scammers use fear tactics to pressure victims.
- ✔ **Register your phone number with "Do Not Call" lists** – Reduces scam calls.
Smishing (SMS Phishing)
Smishing is a **social engineering attack via SMS (text messages)**, tricking victims into **clicking malicious links, installing malware, or sharing credentials**.
📌 How Smishing Works
- 📲 The victim receives a text message **claiming to be from a bank, courier, or tech company**.
- 🔗 The message contains a link to a **fake website or malware download**.
- 🚨 The victim enters credentials, unknowingly giving them to an attacker.
- 📂 The attacker **uses the stolen data to access accounts or commit fraud**.
⚠️ Real-World Example: Delivery Scam (2021)
Attackers sent fake **"Your package has arrived"** messages pretending to be from DHL and FedEx. Victims entered personal details on a **phishing website**, leading to identity theft.
🛡️ How to Identify & Prevent Smishing
- ✔ **Do not click on links from unknown numbers**.
- ✔ **Verify messages by contacting the company directly**.
- ✔ **Use spam filters** to detect suspicious texts.
- ✔ **Be cautious of messages with urgent requests** (e.g., "Your account will be deactivated!").
Baiting
Baiting involves **offering victims something desirable (e.g., free software, USB devices, or giveaways)** to trick them into downloading malware or revealing personal data.
📌 How Baiting Works
- 📂 The attacker **leaves infected USB drives in public places** (offices, parking lots, airports).
- 💾 A victim **plugs the USB into their computer**, out of curiosity.
- 🐍 The malware **installs automatically**, giving attackers control over the system.
⚠️ Real-World Example: Stuxnet USB Attack
The infamous **Stuxnet malware (2010)** was **spread via infected USB drives**, compromising Iran’s nuclear facilities.
🛡️ How to Identify & Prevent Baiting
- ✔ **Never plug unknown USBs into your device**.
- ✔ **Use endpoint security tools** to block unauthorized external devices.
- ✔ **Train employees to recognize baiting tactics**.
Real-World Social Engineering Attacks
- Twitter Bitcoin Scam (2020): Hackers tricked Twitter employees into giving access to internal systems, allowing them to hijack high-profile accounts (Elon Musk, Bill Gates) and post fraudulent Bitcoin scam messages.
- Google & Facebook CEO Fraud: Attackers stole **$100 million** by impersonating a Taiwanese supplier and tricking executives into wiring funds to fraudulent accounts.
- iSpoof Scam (2022): A large-scale call spoofing attack led to **£100 million** in financial fraud.
How to Protect Yourself from Social Engineering
- ✔ **Think Before You Click:** Verify links before opening.
- ✔ **Enable Multi-Factor Authentication (MFA):** Adds extra security.
- ✔ **Verify Caller Identities:** Banks and IT staff will never ask for login credentials over the phone.
- ✔ **Be Wary of Urgent Requests:** Scammers create panic to manipulate victims.
- ✔ **Use Strong, Unique Passwords:** Prevent attackers from accessing multiple accounts.
Social Engineering Lifecycle
This diagram illustrates the different stages of a social engineering attack, from the initial approach to exploitation and execution.
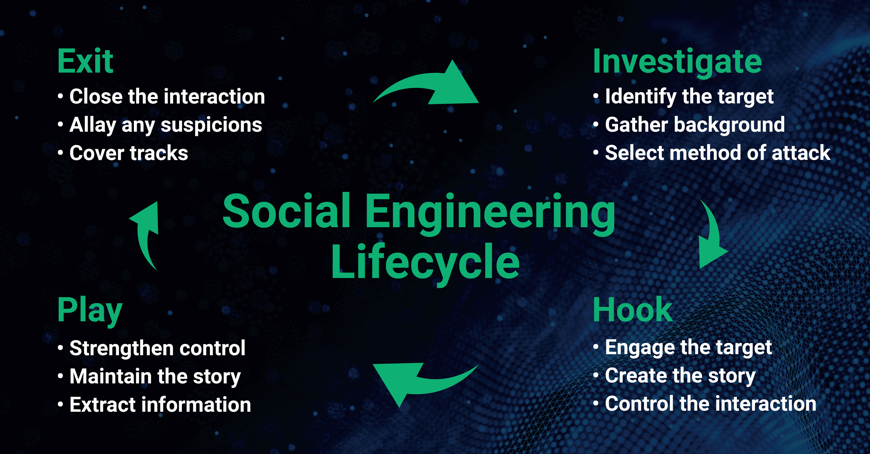
Understanding these stages can help recognize and prevent attacks before they succeed.